It’s important to examine digital rights management before delving into how it’s provided to you as a customer. Digital Rights Management, or DRM, is a technology that restricts the usage of digital content, usually through encryption. DRM systems intend to protect content creators by ensuring that authorized users see their content or use it correctly. Digital rights management (DRM) vendors sell software that allows you to restrict how your customers can use protected digital content. Without it, unauthorized users might steal your digital content, leaving you with no money earned and pirated content.
DRM vendors help prevent piracy by developing complex software that prevents people from copying content they haven’t paid for. The content is encrypted using a key only available to someone who has paid for the content. DRM vendors provide you with an encrypted version of the content you have purchased. The provider usually distributes the content with a license that determines how the content gets used.
Table of Contents:
- What is DRM (Digital Rights Management)?
- How does a DRM Vendor works?
- What Steps are required to become a DRM Vendor
- Why need DRM Vendors and DRM Providers?
- Benefits of using DRM Vendors and DRM Providers
- Challenges in implementing DRM and need of DRM Vendors
- VdoCipher – Best DRM Vendor to protect your Video Content
- Best DRM Vendors for eBooks and Brand Protection
- FAQs
What is DRM (Digital Rights Management)?
Digital Rights Management (DRM) is a critical tool for creators and publishers of digital media, aiming to safeguard their profits and intellectual property. With the rise of personal computers, it has become exceedingly simple to replicate digital files countless times without losing quality. DRM serves as a means to control and monitor the distribution and usage of digital media, thereby curbing the unauthorized sharing of copyrighted content.
At its core, DRM systems protect digital content by either encrypting it, allowing access only to those with proper authorization, or by embedding digital watermarks that deter unauthorized distribution. These measures ensure that only paying customers, who have legally acquired the rights, can access and use the content.
In many jurisdictions, such as the United States, circumventing DRM protections is illegal, highlighting the legal backing that supports the enforcement of these digital rights. DRM is therefore seen not only as a technical solution but also as a legal framework designed to control the use and dissemination of digital assets, exclusively applicable to digital or digitized media.
How does a DRM Vendor works?
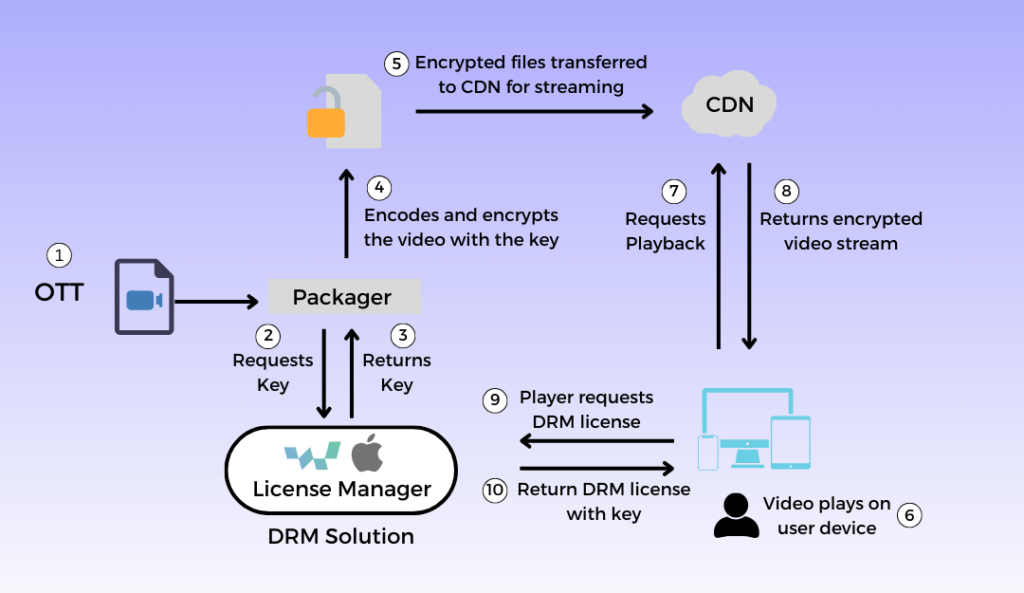
Digital Rights Management (DRM) mechanisms function by securing content through encryption, ensuring that only authorized users who possess the decryption key can access it. The DRM process, particularly for video content, involves multiple parties including the content provider, packager, Content Delivery Network (CDN), DRM platform, and the player. Here’s an overview of how DRM works in four key steps:
Explore More ✅
Protect your videos with the same technology that powers Google devices and browsers. Learn more about VdoCipher’s Multi-DRM solution!
Step 1: Encrypt the Content
The initial and most fundamental step in DRM is encryption. This process converts plain data into ciphertext using a key, making the content unreadable to anyone without the corresponding decryption key. The Advanced Encryption Standard (AES) is commonly used due to its efficiency and simplicity in key management, as it uses the same key for both encryption and decryption.
Step 2: Key and License Management
The encryption key is usually generated by the content provider and handed over to the packager or transcoder for encrypting the content. In DRM systems, this process is often enhanced with tools from DRM vendors to manage and generate keys securely.
Step 3: KeyID and ContentID
Once the content is encrypted with a key provided by a DRM vendor, identifying the correct key for decryption is crucial. This is managed through a KeyID, which acts as an identifier for the key, and a ContentID, which is a unique identifier for the content. Both identifiers are packaged within the license, stored securely on a License Server.
Step 4: Decryption and Playback
During playback, if a video is encrypted, this information is flagged in the manifest file. The player, upon attempting to play the video, requests the license from the DRM server using the license URL provided in the manifest. If the server validates the request, it issues a license containing the decryption key, which the DRM modules within the player use to decrypt and play the content.
This simplified overview covers the basics of DRM operations. However, the full implementation can be more complex, involving additional features such as key rotation, particularly for live streaming services.
| Decade | Milestone |
| 1980s |
Introduction of Software Service System (SSS) by Ryuichi Moriya, a pioneering DRM technology based on encryption with dedicated hardware for decryption.
|
| 1990s |
Passage of the Digital Millennium Copyright Act (DMCA) in the US, criminalizing technologies that circumvent DRM.
|
| 2000s |
Apple’s iTunes implements DRM, restricting songs to play on only three computers and limiting playlist copies, exclusive to Apple devices.
|
| 2010s |
Emergence of FairPlay Streaming by Apple, and adoption of DRM by major streaming services like Spotify and Netflix, enabling secure browser and app access.
|
| Today |
Expansion of streaming market with services like Amazon Prime, DisneyPlus, Hulu, HBO Max, etc., all utilizing DRM to protect digital video content.
|
Why need DRM Vendors and DRM Providers?
Flawed Implementation – The root cause of DRM malfunctions is the inconsistencies in implementing DRM. It can lead to a lousy user experience or security breach. From UX designing to software diversity, collaborative integration must occur between users and DRM vendors.
End-user adaptability – The other common issue in DRM implementation is End-user adaptability. With the growing number of new devices and on-demand content consumers, the delivery model, licensing, and content management needs implementation. Educating former and existing customers about the various new updates and changes is a task to handle with better customer support.
Lack of all-in-one DRM solutions – Instead of subscribing to multiple DRM vendors, most end-users look for an all-in-one DRM solution. Implementing a unified DRM solution for digital content requires workforce, investments, and levels of technical implementations.
Security and IP protection – DRM vendors can effectively manage access to digital assets by employing IP geolocation. IP geolocation data needs to be up-to-date and standardized. It simplified the licensing rights authentication across regions and authorized users’ access. DRM vendors need to securely store a vast amount of Intellectual Property data and create a workflow for users to manage and track their content. If there is a bug in the DRM software that allows people to copy content without paying for it, then it is easy for people to pirate content. DRM vendors have to address this issue by implementing multiple security layers, IP protection, watermarking, and of course, customer satisfaction.
What Steps are required to become a DRM Vendor
- Acquiring DRM license permissions
- Setting up storage infrastructure
- Encoding
- Transcoding
- Using the license encryption keys to encrypt the digital content
- Storing the encrypted file
- CDN setup
- Authorized access management
- Request processing via license server
- Decrypt the requested resources via the license server
- Allow playback or opening of a file through a DRM player or viewer
Benefits of using DRM Vendors and DRM Providers
The main benefit of using a DRM provider is the ease of implementation. A DRM provider is a company that provides technology and services to help content owners and distributors protect their intellectual property. DRM providers offer a variety of services, including digital rights management, content security, and anti-piracy measures. They work with content owners to help them protect their copyrighted material and ensure that it is not illegally copied or distributed.
Most DRM providers offer APIs that are easy to use and will take most of the implementation burden off your shoulders. Additionally, you get a lot of additional functionality out of the box, such as a wide array of supported devices, reporting, and even analytics.
The great thing about this is that you don’t have to build all of it yourself. It frees up your time and resources to focus on other areas of your business. You also get support and the latest updates from the provider. You’ll easily integrate any newly added features in the future.
You may also have the option of building your custom reporting based on the provider’s data. It will give you a lot of insight into the performance of your eBooks or video content and the customers who purchase them. In other words, when you register your work with a DRM provider, you can make your work securely available, in multiple formats and across multiple platforms, without having to know about all the logistical details of digital rights management. You can focus on your work, and the provider will worry about making your work available.
Explore More ✅
Experience the ultimate viewing with VdoCipher’s Widevine DRM. No plugins, just seamless, secure streaming. Stream your video content today!
Challenges in implementing DRM and need of DRM Vendors
DRM license providers usually don’t sell directly to customers. Instead, they sell to software and media companies, which then sell their products to end-users like eLearning companies.
When it comes to digital rights management implementation, there are three main challenges: security, compatibility, and interoperability.
- The first challenge, security, is an important topic of concern. One of the most common threats to digital rights management is hacking. Hackers can bypass DRM systems and gain access to protected content. Content providers and publishers must ensure that the content they protect is secure against hackers.
- The second challenge, compatibility, is also a major concern. DRM must be compatible with many different types of devices. If the DRM is not compatible, it can be highly limiting.
- The final challenge, interoperability, is similar to the second challenge. DRM must be able to work with multiple technologies and platforms.
VdoCipher – Best DRM Vendor to protect your Video Content
Choosing among the best DRM Vendors for your business needs is a challenging task. It requires considerations on features, pricing, deployment model, customer support, and much more for your businesses. We have listed the best Digital Right Management Vendors for video security, eBooks, documents, and brand protection.
VdoCipher is a secure video hosting solutions provider to LMS platforms, media, e-learning platforms and individual videos creators and helps them in boosting revenue. Vdocipher offers Hollywood Grade DRM Protected Video Streaming to protect videos from piracy and unauthorized access or sharing.
Videos streamed through VdoCipher cannot be downloaded via any software or internet plugins. Using Google Widevine and Apple Fairplay DRM, VdoCipher is serving video content security to over 2000 business customers in more than 40 countries.
- Google Widevine and Apple Fairplay protected DRM encrypted streaming
- Dynamic watermarking and screen capture block
- Live streaming
- API and Plugin Integration
- Multi CDN Integration
- Adaptive and Responsive HTML5 player
- APIs and SDKs
- Geo, IP and Time based restrictions
- Backend Licensing and Authentication
- Best DRM Vendors for eBooks and Brand Protection
- User-based Video Analytics for Piracy Tracking and Hacker Identification
Best DRM Vendors for eBooks and Brand Protection
RedPoint for Brand Protection
Brand intelligence platform, Red Points delivers online brand protection, copyright enforcement, and distributor monitoring capabilities. Red Points gives you full visibility into brands’ presence online. Over 1000 brands and companies rely on Red Points to fight counterfeits, piracy, impersonation, and distribution abuse allowing them to maintain control, improve their brand value, and increase revenues.
- Detect infringers reselling credentials
- Bot-powered scan on marketplaces and social media 24×7
- Photo-analysis
- Self-improving detection
- Potential infringement review in the DRM platform
- Automatic enforcement
Memberspace for Brand Protection
Memberspace is a web application that helps organizations manage their memberships and communications. It allows members to access and update their information, makes it easy to send newsletters and other communications, and provides tools for managing events and activities. With their DRM software, you can protect the existing website and gain new members.
- Access expiration management
- PDF and image protection
- Digital distribution management
- Password management
- Member-only access
Kitaboo for eBooks
Kitaboo DRM is a digital rights management system used to protect e-books from unauthorized sharing and copying. It employs a variety of measures to prevent users from copying, printing, or sharing e-books without permission. Kitaboo DRM is the software to protect the eBooks we publish.
- Publish and secure ebook distribution
- DRM encryption
- Social DRM
- Digital watermarking
- Role-based permissions
- Create a webstore and license your eBooks
- Distribute ebooks to your users from the cloud
- Own branded apps to distribute your eBooks
FAQs
What kinds of content does DRM protect?
Digital rights management is suitable for all kinds of digital content, including everything from novels to computer programs and music. A digital Rights Management system can protect the content which gets digitized.
How is DRM technology applied to digital content?
Digital rights management is often used with digital content delivered over the Internet. When you purchase this type of content, you usually download a copy to your computer. To use the content, you may be required to install a software application. This application will protect the content by preventing unauthorized copying or unauthorized sharing.
What are the points to consider while choosing DRM providers?
Some general considerations are pricing model, market reputation, customization, flexibility in implementation, customer support, the number of countries served, client portfolio.
Supercharge Your Business with Videos
At VdoCipher we maintain the strongest content protection for videos. We also deliver the best viewer experience with brand friendly customisations. We'd love to hear from you, and help boost your video streaming business.


My expertise focuses on DRM encryption, CDN technologies, and streamlining marketing campaigns to drive engagement and growth. At VdoCipher, I’ve significantly enhanced digital experiences and contributed to in-depth technical discussions in the eLearning, Media, and Security sectors, showcasing a commitment to innovation and excellence in the digital landscape.