With the rapid growth of online video platforms, piracy has become one of the biggest challenges for content owners. Whether you run an OTT platform, an online course website, or a paid webinar business, protecting your content is no longer optional. This is where DRM solutions play a crucial role.
In the past few years, there has been an exponential increase in video consumption. According to Statista, in 2019 alone, the number of digital video viewers was 2.6 billion, which is reported to increase to 3.1 billion in 2023. With the increase in the number of viewers, the number of platforms catering to them also increased. A few years back Netflix was the only major player in the video streaming market. But now there are many more platforms, including Amazon Prime, Disney Plus, Hulu, and many more.
With so many streaming platforms available, users often prefer to pirate content rather than pay for a particular platform. In this current scenario, if you don’t focus much on video protection, chances are that your videos will be downloaded and freely available for users. This in turn hurts your revenue by a lot, as users would rather prefer to watch your content for free. The movie industry alone suffers an annual loss of revenue of about 40 and $97.1 billion. If you account for eLearning, personal wellness, and other online platforms, this number can rise even more.
Table Of Content:
- What Is a DRM Solution?
- What Does “DRM-Protected” Mean?
- What Steps are required to become a DRM Solution
- Who provides a DRM license to a DRM Solution?
- Understanding DRM requirements for your business
- What makes DRM Software so essential?
- Why Businesses Need DRM Solutions Today
- How does DRM Software ensure protection for your Videos?
- How DRM Works: Understanding the DRM Process
- DRM as a Service: A Modern Approach
- Choosing a DRM Service provider: what features to look for?
- Use Cases of DRM Solutions
- Choosing the Best DRM Solution
- FAQs
You don’t necessarily have to lose your revenue due to piracy. DRM solutions or Digital Rights Management, solely exist for this purpose- to save your videos from any illegal access.
But then, you might be wondering, what exactly is a DRM Solution? How can it help you? And many more questions. But you don’t have to worry about it, as you’ll get an answer to these questions and more. So, fasten your seat belts and bring out your notepads. Cause this is going to be a ride and not that one filled with just joy and excitement. Which only riddles you with guilt afterward. You’re only going to come out of this journey wiser (hopefully!?)
What is a DRM Solution?
DRM Solution is essentially a Digital Rights Management software package, which ensures that your content is only accessible by anyone you authorize. You can use Video DRM software to make sure that your content is only accessible by the user you authorize and you can even manage the browser or devices they consume your content on.
In a lot of cases even though the videos are encrypted, the key used to decrypt the video is often easily accessible. Any hacker with some knowledge can then easily get access to the encryption key and then access your content. Once he’s downloaded the video it’s then easy to spread it to other pirates
With a DRM server and DRM protected key exchange mechanism, your encryption keys are hidden and aren’t accessible to anyone. This way you protect your videos from any potential hacker or download tools. This makes sure that your content is not pirated and you don’t lose any revenue due to piracy.
In fact, with DRM services or solutions, video platforms tend to see a rise in their revenue. Read this case study by Vdocipher on how users end up raising their revenues up to 990% with the help of a DRM Solution.
DRM services or solutions caters to different forms of content, they can be -video, audio, video games, comics, ebooks, etc. In this blog, I’ll focus on DRM solutions for video and audio streaming.
In simple terms, a DRM system ensures that your video can be watched—but not stolen.
Modern platforms typically rely on video DRM solutions rather than basic encryption because DRM continues to protect content even during playback. This makes it far more effective against piracy.
But before that, let’s have a look at what DRM protected content exactly means.
Explore More ✅
Vdocipher helps several Video Platforms to protect their video content with DRM Encryption
What Does “DRM-Protected” Mean?
The phrase “DRM protected” means that the digital content it is being applied to is restricted in how it can be used. “Digital rights management” is the term that describes a systematic authorization for the use of copyrighted material. DRM protection is applied by using DRM encryption, access control methodologies, a proprietary hardware-controlled environment, a software-enabled black box, and a dynamic key exchange management system. The complete infrastructure regulates copyrighted digital works’ use, modification, and distribution.
A DRM protected content is nothing but the digital content on which DRM protection is applied. Basically, any piece of digital content you protect with a DRM solution would be considered as DRM protected content.
As mentioned in the above section, content becomes DRM protected when you apply a certain set of rules on your copyrighted content to restrict any unauthorized access.
These DRM restrictions are usually against downloading or making a copy of your video. Also, the number of times your videos are being accessed and even the devices on which the video is being viewed. These DRM restrictions can be as simple or complex according to your requirements.
What Steps are required to become a DRM Solution
- Acquiring DRM license permissions
- Setting up storage infrastructure
- Encoding
- Transcoding
- Using the license encryption keys to encrypt the digital content
- Storing the encrypted file
- CDN setup
- Authorized access management
- Request processing via license server
- Decrypt the requested resources via the license server
- Allow playback or opening of a file through a DRM player or viewer
Who provides a DRM license to a DRM Solution?
Since the whole digital ecosystem is dependent on Google and Apple either for devices (hardware) or OS, browsers (software), they are the major DRM license providers. Google provides a license of Google Widevine DRM and Apple provides it for Apple FairPlay DRM. Obtaining a license from them means that you get protection across,
- Desktop/Laptop – Windows, Mac, Linux.
- Browsers – Chrome, Firefox, Edge, Safari, Android Chrome, Edge, Mac Safari, iOS Safari.
- OS – Android, iOS, Android TV, Android TV, Chromecast, IOS App
Understanding DRM requirements for your business
When choosing a DRM service for your business, there are some key aspects to understand.
Accessing content security requirements – While choosing a DRM solution, it is important to evaluate the level of protection your business requires. The various considering factors include the value of your content, the potential risk of piracy and unauthorized access as well as compliance and regulators requirements.
Identifying target platforms and devices – The chosen DRM solution needs to be compatible with the devices and platforms your audience uses to access your content. This includes web browsers, media players, and device types. Identifying this requirement beforehand will ensure seamless delivery for your users.
Analyzing your content distribution strategies – The DRM system should be compatible with the streaming protocol you use such as HLS or MPED-DASH. It should offer features like offline playback, geographic restrictions, and IP/Domain restrictions.
What makes DRM Software so essential?
When content is easily accessible with a single click, protecting intellectual property has become important. Digital Rights Management (DRM) software plays a crucial role in this protection mechanism.
Universal Application – DRM isn’t just for videos. From e-books to software applications, DRM ensures that digital content is only accessible by authorized users. This wide-ranging application makes it a versatile tool in the digital content protection arsenal.
Adaptable Restrictions – One of the standout features of DRM software is its adaptability. Depending on the content creator’s needs, restrictions can be tailored. Whether it’s limiting the number of devices on which content can be viewed or setting a specific geographic boundary, DRM software can handle it.
Combating Piracy – Piracy has become a concerning factor in the media industry. With DRM software, content creators have a robust tool to prevent unauthorized distribution of their content. By encrypting content and ensuring that only authorized users have the decryption key, DRM software effectively combats piracy.
Boosting Revenue Streams – For businesses, especially those in the entertainment and e-learning sectors, DRM software can be a game-changer. By ensuring that content isn’t freely distributed, businesses can maintain their revenue streams, ensuring sustainability and growth.
User Experience – While DRM software is primarily about protection, it’s also about user experience. By ensuring that only legitimate users access the content, businesses can offer a more personalized and seamless experience, enhancing user satisfaction.
Why Businesses Need DRM Solutions Today
As content consumption shifts toward streaming and subscriptions, piracy methods have also evolved. Screen recording tools, stream rippers, and illegal redistribution channels have become more advanced.
This is why businesses now rely on professional DRM services rather than basic security tools. A robust DRM software solution helps:
- protect revenue from content leaks
- meet studio and licensing requirements
- control access across devices and regions
- build trust with creators and partners
For industries like OTT, eLearning, and enterprise training, DRM is not just a feature—it is a foundation.
How does DRM Software ensure protection for your Videos?
Before I take a deep dive into how DRM solutions work, you’ll first need to understand what video encryption is. Then later I’ll show you how a Video DRM solution makes encryption even better to ensure that your videos are protected.
Video Encryption
Video encryption is basically the process of encoding your videos to a non-video secure format. This ensures that no one can’t access your raw video files. When anyone wants to access the file, they’ll only get access to an encrypted file which is just random gibberish.
Encryption can not be broken and the encrypted files can only be accessed with the help of an encryption key. But then the encryption key exchange is where the weakness lies for any standard video encryption technology such as HLS, RTMP or AES-128. Due to the weak key exchange, encryption keys can be accessed by hackers to decrypt and then access the video. This ultimately defeats the initial purpose of video encryption. Although it would hinder anyone with no technical knowledge, anyone with some understanding of how to access the keys can easily work it out and share the video file with others.
DRM-based encryption to protect your videos
DRM takes care of this exact weakness in video encryption and makes sure that the encryption key is not accessible by anyone unless authorized. A video DRM software encrypts the video and even protects the encryption key behind a BlackBox or CDM, which cannot be accessed by anyone. Before going into what a CDM is, you’ll need to know that there are different DRM solutions, which are used together to protect your content.
A typical video DRM service consists of multi DRM, these different DRMS caters to different devices and browsers. These different DRM solutions are:
- Google Widevine DRM solution: It supports Desktop/Laptop (Windows, Mac, Linux) Chrome, Firefox, Edge. Android Chrome, Edge, Android TV, Android TV, Chromecast.
- Apple Fairplay DRM Solution: It supports Mac Safari, IOS Safari, IOS App
- Microsoft Playready DRM solution: It supports Edge in Windows. Windows Edge is also supported by Google Widevine, so Playready is not an absolute necessity.
DRM solution BlackBox the encryption keys in CDM or Content Decryption Module. This CDM, even though on your device, can not be accessed by you. This protects the key as it is kept in the CDM and it can’t be accessed by you or anyone. The only way to access the videos is through Encrypted Media Extensions (EMEs), which are sent via the respective Video DRM System.
As Google and Apple have some control over your browser, OS, hardware or all of these. They can exercise more control and security for DRM encrypted streaming.
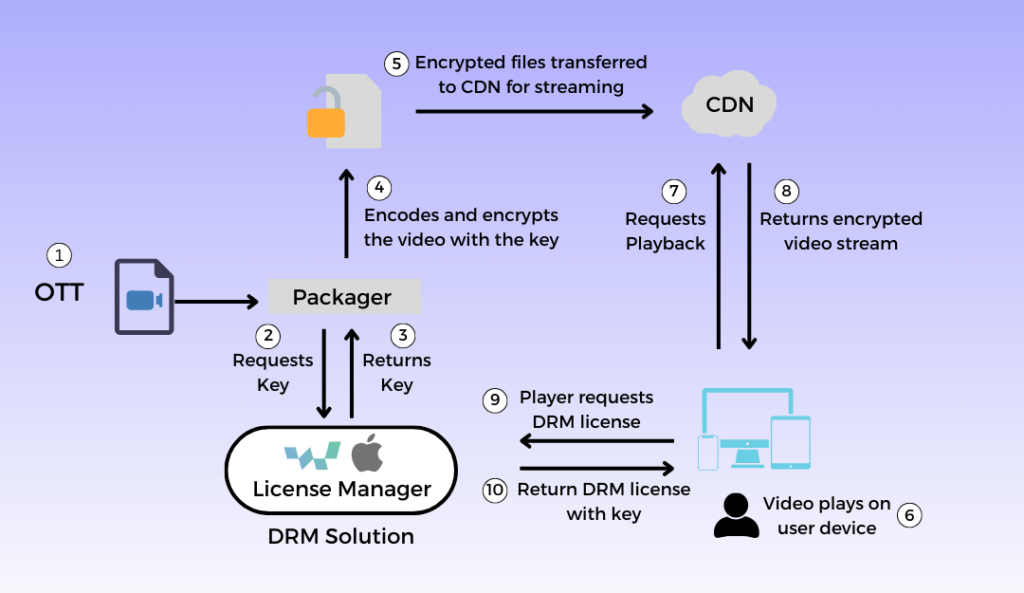
How DRM Works: Understanding the DRM Process
Many people ask, how does DRM work? While the technology behind it is complex, the actual DRM process can be explained simply.
When content is uploaded, it is first protected using DRM encryption software. This converts the original video into an encrypted format that cannot be played directly.
When a user presses play, their device sends a request to the DRM platform. The system then verifies whether the user is authorized based on predefined rules such as login status, subscription validity, device limits, or location.
If all conditions are met, a temporary playback license is issued. The video is decrypted only inside a secure player and cannot be downloaded or shared.
This entire flow explains how DRM works and why it is much stronger than standard encryption.
DRM as a Service: A Modern Approach
Instead of building everything in-house, many companies now use DRM as a service.
With this model, a DRM service provider handles licensing, encryption, playback rules, and device compatibility. This allows businesses to focus on content and growth rather than infrastructure.
Modern DRM service providers offer cloud-based dashboards, APIs, analytics, and scalability, making them the easiest DRM solution for end users and platform owners alike.
Choosing a DRM service provider: what features to look for?
When choosing DRM tools, there are certain features that can make your content even more protected. One of these can be dynamic watermarking, which inhibits users from screen grab video. These are the features that you need to look out for in a DRM Solution:
Encrypted DRM Streaming to Prevent Download
First and foremost is obviously the Video DRM protection. You need to make sure that the DRM service provider supports both Widevine DRM as well as Fairplay DRM. Having the two DRM is an absolute necessity as they pretty much guarantee DRM support on all the major devices.
Screen Capture Blocking
Another major feature you would require is a screen capture block. Even though the video downloads are blocked, users still can record your screen to capture videos. You need to make sure that the DRM Solution you go for stops any type of screen capture.
Dynamic Watermarking with moving user details
Dynamic watermarking helps to discourage any screen capture. You can add the IP address, User-Id, and Email-Id to the screen. Using these, you can identify the point of origin of video piracy.
IP, Geo & Time Based Restriction
Sometimes you need to restrict video playback in certain locations or devices. A Video DRM provider can help you restrict access to a particular Geo/IP. Also, you can put restrictions on total user video playtime.
What are the User Authentication and Acess Control in DRM Services?
In Digital Rights Management (DRM) services, user authentication and access control are pivotal for safeguarding digital content and ensuring that only authorized users can access or interact with protected materials. These DRM features play a crucial role in maintaining the integrity and value of digital assets across various platforms.
User Authentication in DRM Services
User authentication is a foundational component of DRM services, designed to verify the identity of a user before granting access to DRM-protected content. This process typically involves credentials such as usernames and passwords, biometric data, or multi-factor authentication methods. For DRM services, ensuring robust user authentication is critical for preventing unauthorized access and distribution of copyrighted digital content.
Access Control Mechanisms
Access control in DRM services goes hand-in-hand with user authentication. Once a user’s identity is verified, access control mechanisms determine the level of access or the specific actions that the user is permitted to perform with the DRM-protected content. This might include viewing, copying, editing, or sharing digital files. Effective access control is essential for DRM services to enforce content usage policies and comply with copyright laws.
Implementing DRM Services for Secure Content Management
Incorporating user authentication and access control within DRM services involves several steps:
- Designing a Secure Authentication Process: This involves creating a user verification system that can effectively thwart unauthorized access while not detracting from the user experience. DRM services often utilize advanced authentication technologies such as OAuth, token-based authentication, or even blockchain-based identity verification. There is also an option to implement a dedicated ID verification service.
- Developing Dynamic Access Control Policies: DRM services must be equipped with flexible yet secure access control policies that can adapt to different user roles, content types, and distribution channels. These policies should be rigorously tested and updated regularly to address emerging security threats and changes in legal requirements.
- Integrating with Existing Systems: For many organizations, integrating DRM services with existing content management systems (CMS) or customer relationship management (CRM) systems is crucial. This integration allows for seamless user authentication and access control across all platforms where DRM-protected content is available.
- Continuous Monitoring and Reporting: DRM services should include mechanisms for monitoring user interactions with protected content and generating reports on access patterns. This data is invaluable for auditing, compliance, and improving the DRM strategies.
Use Cases of DRM Solutions
DRM is widely used across multiple industries.
- In OTT platforms, OTT DRM solutions and OTT DRM services protect movies, TV shows, and original content while meeting strict licensing requirements.
- In online education, a video DRM solution helps protect paid courses, recorded lectures, and exam preparation material from being copied or resold.
- Corporate organizations rely on DRM platforms to secure internal training videos and confidential content shared with employees.
- Creators, fitness apps, and membership websites use DRM to protect premium content libraries and ensure only paying users can access them.
These real-world DRM examples clearly show why DRM is essential wherever content has monetary or intellectual value.
Benefits of Advanced DRM Services
Implementing sophisticated user authentication and access control within DRM services provides several benefits:
- Enhanced Security: Reduces the risk of unauthorized content access and piracy.
- Compliance Assurance: Helps organizations comply with digital copyright laws and regulations.
- Improved User Management: Facilitates better management of user rights and access permissions.
- Data Insights: Offers valuable insights into how content is being used, aiding in future content strategy and rights management.
Choosing the Best DRM Solution
The best DRM solution depends on your business model, audience, and platform requirements. However, most businesses today look for:
- reliable DRM software solutions
- multi-device and multi-browser support
- scalability for global audiences
- easy integration and APIs
- support from experienced DRM services providers
For streaming businesses, many also ask: what are the best DRM services for streaming media?
The answer usually lies in choosing a trusted DRM solution provider that offers multi DRM support, strong encryption, and seamless playback.
FAQs
What are the challenges of DRM?
One of the main challenges of DRM is that it can be difficult to implement DRM in a way that is both effective and user-friendly.
What type of DRM Solutions are available?
There are a variety of DRM solutions available, each with its own advantages and disadvantages. The best solution includes VdoCipher which has a complete implementation, best infra and accessible support.
What is the result of a lack of video protection?
Ultimately it hurts your revenue by a lot. This revenue loss can be instant or in the future.
Is DRM a solution to Video Piracy?
DRM prevents anyone who does not have the dynamic key from being able to view or use the content. The downside to this solution is that it can be difficult to implement. A solution to implementation is DRM Encrypted Video Hosting providers like VdoCipher.
DRM Solution To Prevent Video Download Piracy
VdoCipher helps media and e-learning platforms to play videos on their website or app in the most secure and smooth manner. VdoCipher ensures their revenues are protected against video piracy. A combination of Hollywood-approved DRM encryption (Digital Rights Management), screen capture blocking, viewer-specific watermarking & licensing technologies ensures that videos can’t be downloaded or shared illegally from a video platform. VdoCipher serves 2000+ business customers from 40+ countries.

Head of Digital Marketing at Vdocipher. I love the art of connecting the right product to their users. When i’m not doing that i love getting lost in books.