The rise of digital media and modern technologies has vastly raised the copyright-owning concerns of organizations and individuals. In just a few clicks of a mouse, many copyrighted images, videos and audio files get downloaded or shared without prior permission. In addition, modern techniques and tools have made it easy to convert media (mostly copyrighted) into various digital forms for easy portability and sharing. This is known as ripping, and the best possible solution to it is using DRM technology. This combines with the internet and hundreds of file-sharing tools (like Torrents) to make unauthorized large-scale distribution of copyright media copies (digital piracy) much easier.
As per a US Chamber of Commerce report, online piracy costs the US economy nearly $30 billion per year. This is where DRM technology comes into play to control and manage access to copyright materials. DRM technology combines a set of applications and technologies to protect digital media against copyright infringements. DRM aims to protect the original copyright holder rights and restrict the unauthorized copying, editing, or redistribution of digital files and proprietary software. Today DRM is playing a leading role in data security.
Table Of Content:
- What is DRM Technology & Protection
- Encryption vs DRM Technology
- Key Players in Digital Distribution via DRM
- Importance of DRM Technology
- DRM Licence : The Root, Leaves and Chains
- DRM Scheme and Transactions Basics
- DRM vs Copyright Laws
- DRM Architecture and How does it Work?
- Types of DRM, its free & open-source providers
- How DRM encryption work
- The need for Multi DRM encryption
- How Industries are benefiting from DRM Software
- Signs of DRM issues while using Netflix, Hotstar, Amazon Prime, Mac, etc
- FAQs
- DRM Vendors
VdoCipher helps ver 3000+ customers over 120+ countries to host their videos securely, helping them to boost their video revenues.
What is DRM Technology & what does Digital Rights Management protected Video mean?
DRM Protected refers to a file that has applied DRM controls to restrict copying, editing or unauthorized content distribution. This includes encryption to prevent unauthorized access and license control for authorizing permissions and access. Here is an example for better understanding. The Apple iTunes Music Store uses DRM solution to restrict the number of devices on which songs are played. The downloaded music files contain the data about purchase and usage activity. Unauthorized devices cannot play the songs. Before installing Microsoft Windows or office software, users must agree to the user license and input the key. A wide range of businesses and professionals are using DRM technology to protect their documents, files, contracts to even employee data.
What DRM does?
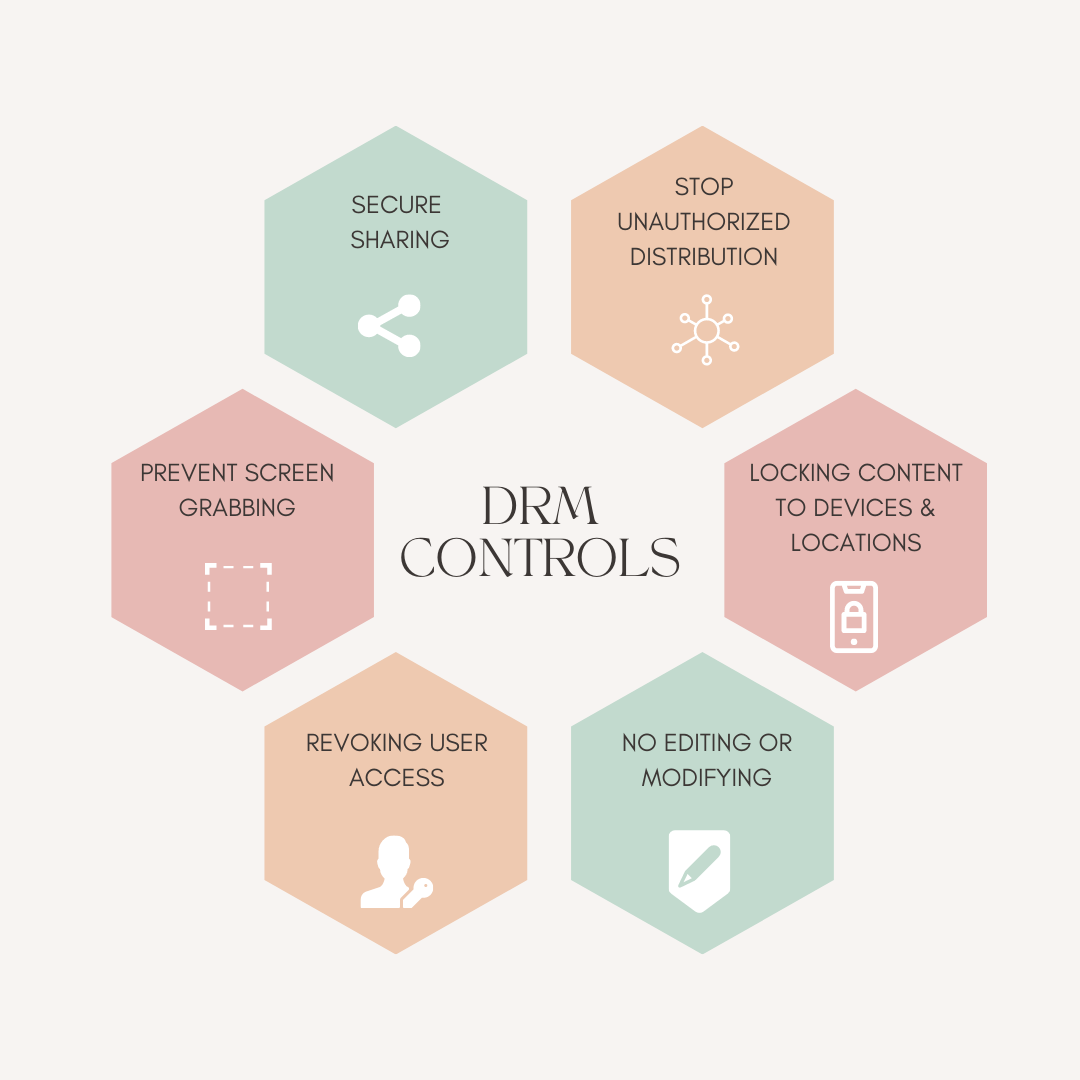
DRM enables content owners and publishers to have control over not only who receives the content but also what they can do with it. Such controls include:
- Only authorized users can access your content.
- Authorized users get access to the content without any 3rd party apps or plug-ins.
- Prevents editing, printing, saving, forwarding, sharing, screen grabbing and more.
- Secure storage and distribution of content between collaborators during production.
- Content limited to devices, IP addresses and country locations.
- Watermarking to establish identity.
- Access gets activated or revoked anytime
Meaning of DRM protected Video?
When you upload a video on a website for users, the main concern is whether the content is safe or not. There are probable chances of someone downloading or misusing the content if not secured. DRM technology in respect of video ensures encrypted transmission so that only authorized devices and users can watch it. For better device compatibility Multi DRM is used to encrypt and package the video content. When a user attempts to play a video, the online video player requests a key from the licensed server. Before issuing a decryption key, the DRM license server authorizes the user and the device. The player decrypts and the content is played back for the user after receiving the decryption key.
DRM Software
DRM Systems can get implemented as a hardware solution (hardware DRM) or software. Hardware DRM appliances include video game consoles, tablets, personal computers implementing secure boot. Digital Rights Management (DRM) software is an application tool combined with a set of policies and procedures for copyright protection and unauthorized content access. DRM software encodes the file with access control settings defined by the owner or copyright holder.
Encryption vs DRM Technology
Though encryption is key in shielding digital files, it’s not foolproof. It doesn’t block file copying but rather restricts content access. DRM technology, however, shares encryption’s focus on controlling access and use, not copy prevention. Grasping these nuances helps reveal how encryption fits within DRM systems to protect digital content.
Picture this: selling an encrypted ebook to Jane. If the seller gives Jane the ebook and decryption key, the cat’s out of the bag. Jane can share both with anyone. In this scenario, encryption flops, as the key holder has no incentive to protect the file.
A safer approach: give Jane’s computer the key, not Jane. She downloads the encrypted ebook and a separate, encrypted key file (a “voucher”). Jane’s ebook software decrypts the voucher, and presto, ebook access—Jane never lays eyes on the key. Yet, even this method isn’t foolproof, as Jane could send both files to a friend, who could then access the content.
To amp up security, DRM can tether the key to Jane’s hardware. When Jane buys the ebook, her computer’s unique hardware ID goes to the seller. The voucher has this ID, and the software checks for a match before opening the file. No match, and no access to different machines.
Linking digital files to specific hardware is common in DRM, but it’s not without issues, given the hardware’s brief average lifespan. A cutting-edge solution would connect files to people, not devices, allowing smooth file transfers between machines. Enter “trusted systems,” potentially DRM’s next evolutionary step.
While encryption is a powerful tool for protecting your video content. However, DRM has its limitations. Learn more about why is DRM not enough to protect video piracy and what you can do to secure your content effectively.
Key Players in Digital Distribution via DRM
In the realm of Digital Rights Management (DRM), we’re primarily concerned with two essential content aspects. To illustrate:
- Rights Management: Legal rights holders must identify, gather metadata, assert rights, and develop business models for their content distribution. They should also provide client access via surveys.
- Rights Enforcement: Enforcing usage rules and rights for content is critical, posing a significant challenge in DRM solutions.
DRM technology systems involve four key players in digital media distribution (multimedia, documents, music, etc.):
- Creators: Those who create and legally own the content (documents, videos, music, etc.).
- Producers: They transform the content into a digital product, wrap and safeguard it.
- Distributors: They promote and sell digital products to consumers.
- Consumers: The paying clientele who enjoy digital content.
In certain scenarios, these roles may merge, such as the first two entities often referred to as the content provider. Introducing these entities necessitates a new subsystem in digital content delivery: the licensing subsystem. This subsystem comprises a licensing service (LS), responsible for issuing consumer rights, and client components that enforce those rights.
Importance of DRM Technology?
Stealing and copying someone else’s work and ideas has been long here. However, with technological advancements, digital piracy is sharply rising. Sensitive company documents, video footage, and multimedia content is every second getting remixed, reused, and republished. Anyone having an internet connection can access these files. Consequently, these digital assets need proper protection. With DRM, access to these resources gets restricted, and no one can do whatever they want to the intellectual properties and media files.
In our rapidly evolving digital world, DRM technology’s relevance is ever-growing. Picture this: you’ve borrowed a hardcover book from the library, and you yearn for your own copy. While copyright law may frown upon replicating it, no tangible barrier stops you. However, you’re deterred by the labor, expense, and subpar outcome of duplicating a physical book.
Now, envision possessing that same book, but digitally. Copying is a breeze—practically instantaneous, free of charge, and yielding an impeccable replica. Moreover, digital files make generating several copies and disseminating them a cinch. Although copyright laws shield both physical and digital books, the simplicity of duplicating digital content demands sturdier protection.
Enter DRM technology. Since copyright laws can’t fully thwart unauthorized copying and distribution, a tech-based approach, like DRM, becomes indispensable in safeguarding digital assets. This potent protective measure empowers creators and copyright owners to retain control over their digital creations amidst an evermore interconnected world.
Digital Rights Management (DRM) is essential for protecting digital content, ensuring fair use, and securing intellectual property. DRM technology prevents unauthorized access, copying, and distribution of DRM-controlled content. Below are key reasons why DRM protection is crucial in various industries.
1. Prevents Unauthorized Distribution & Piracy
- DRM security helps in restricting users from copying or sharing DRM-protected digital content without permission.
- It combats piracy, which leads to major revenue losses for content creators and publishers.
- Without DRM solutions, digital media such as movies, music, eBooks, and software can be easily duplicated and illegally shared online.
2. Protects Intellectual Property (IP) Rights
- DRM systems safeguard the intellectual property of content creators, software developers, and media producers.
- DRM software ensures that their work remains secure from unauthorized modifications or reproductions.
- By using DRM encryption, creators maintain control over how their content is accessed, modified, or distributed.
3. Ensures Revenue Generation for Content Creators
- DRM protection ensures that artists, publishers, and developers get paid for their work by preventing unauthorized use.
- Streaming services such as Netflix, Spotify, and Amazon Kindle use DRM digital rights management to enforce subscription-based access.
- Various monetization models, such as pay-per-use, subscription-based access, and one-time purchases, are secured through digital rights management software.
4. Enables Secure Digital Distribution
- DRM solutions enable secure online distribution of digital content, allowing businesses to confidently sell and stream media.
- DRM technology ensures that only authorized users can access and download digital media, preventing unauthorized alterations.
- Secure distribution is crucial for video streaming services, DRM-controlled content, and DRM-protected media.
5. Supports Different Licensing Models
- Types of DRM allow content providers to implement various licensing models, such as:
- Time-based access (e.g., rental services like Amazon Prime Video)
- Subscription-based access (e.g., Netflix, Spotify, Disney+)
- Pay-per-download (e.g., Apple iTunes, Google Play Movies)
6. Helps Enforce Regional Restrictions
- DRM systems allow content providers to restrict access based on geographic locations.
- Streaming platforms like Netflix, Hulu, and Disney+ use DRM protection to comply with regional licensing agreements.
- Without DRM technology, cross-border access violations would be difficult to prevent.
7. Enhances Digital Security & Data Protection
- DRM security helps prevent unauthorized modifications, tampering, or reverse engineering of DRM software and digital files.
- DRM encryption secures content from cyber threats, ensuring that only authorized users can decrypt and access DRM-protected media.
- This is especially important for sensitive corporate documents, confidential research, and government data.
8. Regulates Corporate & Educational Content
- Businesses use digital rights management software to protect DRM-controlled video content,
- Educational institutions use DRM software to restrict access to DRM-protected videos
- DRM solutions ensure that educational content is accessed only by authorized students or faculty members.
9. Maintains Brand Reputation & Compliance
- Unauthorized distribution of DRM content can lead to copyright infringement, legal issues, and financial losses.
- DRM protection helps businesses comply with digital rights management (DRM) laws, copyright regulations, and industry standards.
- Protecting DRM-controlled content safeguards a company’s reputation by preventing leaks and unauthorized modifications.
10. Provides Content Usage Analytics
- Many DRM solutions include tracking and analytics features, helping content providers monitor how DRM-protected media is consumed.
- Digital rights management software helps businesses analyze user activity to refine marketing and content strategies.
- By tracking DRM-controlled content, providers can detect piracy attempts and enforce DRM security more effectively.
DRM Licence: The Root, Leaves, and Chains
A license, a crucial data file, holds an asset’s decryption key (either another license or content). Coupled with DRM rights and restrictions, it defines content usage parameters. Licenses come in three distinct flavors:
- Simple License: A DRM License, sourced from a DRM Server-built application, containing rights, restrictions, and a key for the corresponding content.
- Root License: Governing one or multiple leaf licenses, it controls playback for various content pieces. For instance, in a subscription model, the root license may expire, while the leaf licenses don’t. When the root license expires, the leaf licenses become unusable until a new root license is obtained.
- Leaf License: A simple, root license-dependent license.
Imagine a user with a subscription who has downloaded several videos for offline viewing. Each video possesses a leaf license, outlining its permissible usage. Let’s assume the leaf license permits video playback anytime. However, DRM technology mandates a valid root license for playback. If the root license expires (possibly due to an expired subscription), the leaf license disallows playback. In this manner, the root license governs the entire subscription (including all leaf licenses on the user’s device).
DRM Scheme and Transactions Basics
In the DRM scheme, various entities like content providers (CP), distribution services (DS), license servers (LS), certification authorities (CA), and clients (C) work in tandem, adhering to DRM protocols and design patterns detailed earlier. The CP generates content, which is then securely transmitted to DS. This occurs in a protected environment employing SSL, HTTPS, SRTP, FTPS, and the like, so security concerns between CP-to-LS or CP-to-DS are negligible.
DRM transactions can be broken down into distinct phases:
- Crafting content, rights, metadata, and containers
- Key generation
- Content requests
- Client authorization
- Distribution of licensing info and rights-objects
- License acquisition, interpretation, and utilization
- Content consumption
During the final stage, content consumption, crucial security measures must be in place within the client subsystem as content is decrypted and rendered. In this ecosystem, any security breaches in the client component jeopardize the entire content protection strategy. Bearing these risks in mind, DRM-enabled content delivery systems should incorporate mechanisms to address potential client component corruption.
A PKI-based framework where the public key is shared and used to validate the identity of the person transmitting the data and to decrypt the data itself is suggested. This is for DRM architecture tailored to business-specific environments, offering cryptographic support for entity authentication and usage rights protection via asymmetric encryption of license objects. Shielding these objects, uniquely issued for each user request with a license issuer’s private key, also ensures service non-repudiation.
Users should avoid sharing their private keys and certificates, as unauthorized parties could exploit them to purchase content at the original user’s expense. The DRM component interactions contribute significantly to the overall DRM system, with the “middleware” playing a vital role in guiding interaction policies. This middleware entity is responsible for signaling delivery and licensing services to confirm that only legitimate users access the system.
Positioning the middleware component as a cloud-based service makes it accessible to users across various devices. Additionally, a user’s personal computer can serve as a distribution service provider for their domain of devices, reducing internet connectivity reliance. The protocol outlined earlier in this section ensures heightened security for users and content management by handling each user and content request autonomously.
DRM Technology vs Copyright Laws
A common question arises: “Do I retain fair use rights?” Absolutely, copyright law still upholds your fair use rights. However, DRM may hinder the exercising of those rights. It’s not a copyright law implementation but a digital work protection system. As the fair use and first sale rights debate for digital materials continue, most DRM system creators steer clear of copyright law references in their products. Instead, DRM enforces licenses via software controls, reflecting grants expressible in a computer environment rather than traditional copyright law rights.
Imagine a license allowing up to five book pages to be copied. If you need six pages and believe fair use permits it, the software still restricts you to five. Unlike copyright law’s flexible nature, DRM systems are quantitative.
A notable contrast between DRM and copyright law, causing concern, is that copyright law outlines a few copying and performance rules, granting exclusive copyrights to rights holders and listing some exceptions. It doesn’t attempt to foresee every copyrighted work usage. DRM, on the other hand, operates oppositely. While copyright law implies “everything not forbidden is permitted,” DRM adopts the “everything not permitted is forbidden” stance. With DRM, actions like printing must be explicitly granted; otherwise, the system disallows it. DRM developers see this as a necessary security measure, but it carries significant implications for future protected work usage.
Picture a decade from now, when computers project displays onto any surface instead of using screens. If the DRM technology system doesn’t recognize this as an allowed action for a specific digital resource, it won’t permit viewing on future computers. Consequently, it might become impossible to view the resource at all, as the DRM controls won’t acknowledge the technological shift. This potential DRM and innovation interaction could suppress both innovation and access to intellectual resources.
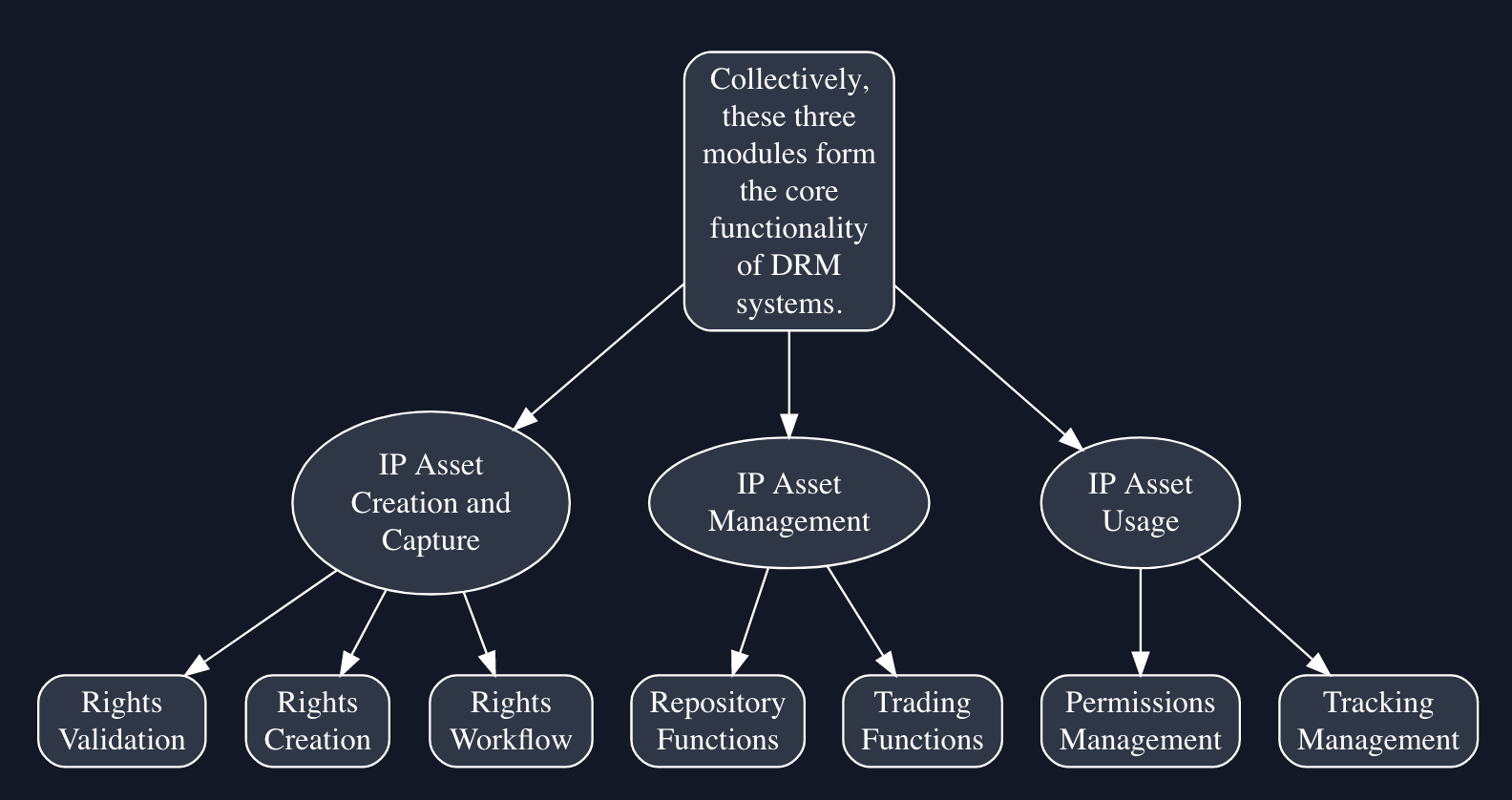
DRM Architecture and How Does DRM Work?
DRM architecture lacks a standard, with multiple frameworks provided by various vendors. However, the DRM framework can be divided into three areas:
- IP Asset Creation and Capture: This pertains to content management and creation for streamlined trading. It encompasses asserting rights when content is initially created or reused by content creators/providers. This module offers:
- Rights Validation: Ensures existing content rights when creating new content.
- Rights Creation: Assigns rights to new content, including identifying rights owners and usage permissions.
- Rights Workflow: Processes content through workflow steps for rights and content review or approval.
- IP Asset Management: Involves managing and enabling content trade. This includes receiving content from creators and incorporating it into an asset management system, which manages descriptive metadata and rights metadata (parties, usages, payments, etc.). This module includes:
- Repository Functions: Accesses and retrieves content and metadata from possibly distributed databases.
- Trading Functions: Issues licenses to parties after rights agreement for content.
- IP Asset Usage: Refers to content usage after trading. This encompasses supporting traded content constraints within specific desktop systems or software. The IP Asset Usage module features:
- Permissions Management: Enforces rights associated with content in the usage environment (e.g., disabling printing if the user can only view the document).
- Tracking Management: Monitors content usage when tracking is part of the agreed-upon license conditions (e.g., limiting video plays to ten times).
Types of DRM, its free & open-source providers
There are many DRM solutions to protect video content. The most popular types of DRM solutions/services supporting common web browsers, devices, and set-top boxes are:
Widevine DRM: Google’s Widevine DRM is compatible with Chrome, Firefox, and Edge browsers, Android, and Chromecast devices. Widevine DRM supports HLS, MPEG-DASH, and MSS streaming with CENC and CMAF. There are two versions of Widevine, Classic, and Modular.
FairPlay DRM: DRM solution from Apple, FairPlay DRM securely delivers streaming media using HLS (HTTP live streaming) protocol. It has native support on iOS, tvOS, iPadOS, watchOS 7, macOS AND Safari browsers.
Open Source: There are GitHub repositories on open-source DRM solution, but most of them don’t get updated frequently. Also, there is a fundamental problem with open-source DRM solutions. Even though all of the algorithms & source code can be publicly available without harming the core security principles, client devices need to be trusted & verified by the rights issuer to do anything forbidden or restricted. This is incompatible with FOSS licensing guidelines, which elaborates that the user of a device should always have complete control over what the device does.
OMA DRM: OMA DRM, a digital rights management (DRM) system, was developed by the Open Mobile Alliance. Its members include mobile phone manufacturers (such as Nokia, LG, and Samsung), system manufacturers (like Ericsson and Siemens), network operators (Vodafone, O2, and Orange), and IT companies (Microsoft, IBM, and Sun). This DRM system allows content creators to enforce limits on usage and duplication by customers. Many modern phones feature OMA DRM, which has two versions: 1.0 and 2.0. To guarantee compatibility among all OMA DRM implementations, the Open Mobile Alliance supplies specifications and testing tools.
How does DRM encryption work?
DRM Content Encryption
In an IP-based DRM system, the content is encrypted using DRM OEM specifications. The license key contains the licensee or owner’s digital rights as rights objects. Most solutions are using technologies designed around 128-bit AES encryption using CTR or CBC modes. Both of these modes are part of Common Encryption (CENC) and encrypt streams to deliver securely. The video player decrypts the encrypted streams using DRM licensing.
The simplest method of packaging content is through the command line interface packager. CLI tools lack complexity, support hooks, error messaging, and more. Next are the server-side tools to provide content encryption. These tools will provide the necessary chinking, and fragmentation to prepare packaging of formats like MP4 into adaptive bitrate streaming files. Server-side encryption offers greater scalability, security, advanced API calls, parallel packaging, and more.
To encrypt content, the packager requests an encryption key from the DRM server. The DRM server provides an encryption key and links that key to the content ID. Using the encryption key, the packager encrypts and re-packages the content.
DRM Playback & two ways of DRM Encryption
There are two ways to encrypt the content using streaming servers. One is Pre-Encryption and the other is Just-in-Time.
Pre-Encryption: In this model, the server encrypts the content at the time when it is ingested or uploaded. The content gets stored and streamed when requested. The server cues and encrypts the content when the server’s systems are optimized i.e; during low-demand periods. Servers implementing pre-encryption can handle more streaming connections and are more secure.
Just-in-time: In this model, the server stores the content raw. When a user makes a request, the server instantly starts to encrypt it and feed out the streaming interface to the CDN and user. Such servers are susceptible to performance issues under significant load. In addition, the server storage is full of encrypted master files and requires a robust security system in place.
Playback: To enable DRM playback on the player side without plugins, decrypted playback uses HTML5 encrypted media extensions (EME). For MPEG-CENC Multi-DRM encrypted content, the player can auto-choose the natively supported DRM.
The need for Multi DRM encryption?
Not all viewers watch content on the same platform and browser. Each platform and browser support a single DRM encryption. To ensure complete coverage across all screens, multiple DRM encryptions are required. MPEG Common Encryption (MPEG-CENC) standard makes DRM implementation effective. MPEG-CENC allows multiple DRM encryptions on a single video. It’s up to the video player to decide which encryption must be activated based on the platform/browser. In fact, Apple browsers and devices are exceptions to the MPEG-CENC standard, which instead require HLS packaging.
How Industries are benefiting from DRM Software?
eLearning Organizations: They have a great need to apply Video DRM solutions as they are the most vulnerable. Making an educational video is itself a tedious task and protecting it from piracy is again a technical mechanism. This technical mechanism is hard to implement and most of the eLearning platforms use services from DRM enabled secure video hosting providers like VdoCipher.
Standard Organizations: National standard organizations or industry associations have the most pertinent information that professionals need. Companies and professionals pay subscriptions or membership fees to access these documents. Such organizations need to have their documents, audio, video files encrypted so that only authorized members access them. A DRM solution can be useful to secure these contents down for a certain audience.
Media & Publishing: For media and publishing houses, content is everything. Protecting the content is their bottom line. Unfortunately, the content gets shared with subscribers, and there arises leaks, piracy, unauthorized access and more. This holds the same for self-book publishers.
Vdocipher helps several VOD Platform to host their videos securely, helping them to boost their video revenues.
Financial Services: Financial institutions like insurance companies, equity firms, asset management companies need to protect the data of their clients and shareholders. Solutions like ‘Dropbox’ secure the portals where clients access the files but don’t protect individual files once downloaded. A DRM solution protects the downloaded files, irrespective of where they get saved or stored.
Signs of DRM issues while using Netflix, Hotstar, Amazon Prime, Mac, etc
- No sound, but the title plays
- Background sound but no dialogue
- Disc stucks on the title page or loading screen
- The movie stops in the middle of playback, or scenes play out of order
- The video freezes or skips
- Pixelated or distorted picture
- Troubleshooting DRM issues on Hotstar, DR-1100 Playback Error
- This error generally occurs due to a downgraded Hotstar app or an unsupported device. To watch DRM protected videos, one needs to have a DRM supported device and a valid Disney+ Hotstar subscription.
Fix DR-1100 error on Android Phone & TV
- Update or download the latest Disney+ Hotstar app
- Install the DRM Info app from the Google play store and check the security level. DRM content will only play if the security level is L1, not L2 OR L3.
- Try to replay the video title again in the Hotstar app and if it shows an error, then try using a different browser. Also, verify that the device isn’t rooted.
- On clearing Data/Cache followed by TV OS update and restart, the error is fixed on Android TV.
Netflix Error N8156 6013
Sometimes while playing videos on Netflix via a web browser, an error is thrown. “Whoops, something went wrong… Digital Rights Management (DRM) Error. We’re sorry, but there is a problem playing protected (DRM) content. The date on your computer is 12/17/2012, which may be incorrect. Please correct the date on your computer and try again.”
This error is related to the Silverlight plugin used by the browser to play Netflix. It requires using a browser supporting HTML5. (Edge, Safari, Chrome, Firefox, Opera)
Fix error on Mac computers
- Quit all browser instances
- Go to Library/Application Support/Microsoft/ folder
- Under it, delete the PlayReady folder
- Verify that you have the administrative rights on your OSX profile
- Try to replay the video title again and if it shows an error then try using a different browser.
Fix error on Windows computer
- Quit all browser instances
- Search C drive for mspr.hds
- Under search results, delete all the mspr.hds files
- Verify that you have the administrative rights on your Windows user account
- Try to replay the video title again and if it shows an error then try using a different browser.
Amazon Prime Video Error 7235 on Chrome - Make sure the Chrome web browser is up to date. Navigate to Settings > About Chrome for the available browser updates.
- Type chrome://components in the chrome web browser and hit enter. Under Widevine Content Decryption Module, click ‘Check for Update’. Install any available update.
FAQs:
What is TPM DRM?
Trusted Platform Module TPM (ISO/IEC 11889) is a dedicated microcontroller to provide security capabilities at the hardware level using integrated cryptographic keys. Generally speaking, the term refers to a chip conforming to the standard.DRM tools use TPM functionalities like device authentication. Windows Defender, software license enforcement, Windows Domain Logon and many more use TPM chips.
How to check if a video is DRM Protected in Windows 10?
- Select the desired multi-media file
- Right-click on the file and select ‘Properties’
- Select the ‘Details’ tab and scroll down to the ‘Protected’ selection.
- The ‘Protected’ field will show ‘Yes’ or ‘No’. ‘Yes’ indicates DRM protected file.
Why CENC standard allows two encryption modes, AES-CTR and AES-CBC?
We use both the standards for encrypting video content and are not compatible with one another. It is due to the encryption cipher supported by each DRM system. However, Apple FPS supports only AES-CBC, while Google Widevine supports both modes. Service providers deliver content to various devices using HLS or MPEG DASH streaming format, which vary in support of DRM systems. To cater to this fragmentation, CENC allows both modes.
What are DRM Vendors?
Basically, DRM vendors are media tech companies like VdoCipher. They offer complete integrations including your video hosting and distribution over CDN with all advanced video security features. The complete package lets you safeguard your video on all devices supported by inbuilt Google Widevine or Apple Fairplay. These packages also include Adaptive bitrate streaming for various bandwidths and multi-device support.
What is DRM protection?
DRM protection refers to security measures implemented to restrict access, copying, or modification of digital content, ensuring only authorized users can use it.
What is DRM encryption?
DRM encryption is a method of securing digital content by encoding it so that only authorized users with the proper decryption key can access it.
What is DRM in digital media?
DRM in digital media ensures that music, movies, eBooks, and other online content are used only in compliance with licensing agreements, preventing piracy and unauthorized sharing.
What is digital rights management in Android?
Digital Rights Management in Android refers to the DRM technologies used by Android devices, such as Google Widevine, to secure streaming content and prevent unauthorized copying.
How can users legally access DRM-protected content?
Users can legally access DRM-protected content by purchasing or subscribing to licensed services, using authorized devices, and following the terms of use specified by content providers.
Supercharge Your Business with Videos
At VdoCipher we maintain the strongest content protection for videos. We also deliver the best viewer experience with brand friendly customisations. We'd love to hear from you, and help boost your video streaming business.


My expertise focuses on DRM encryption, CDN technologies, and streamlining marketing campaigns to drive engagement and growth. At VdoCipher, I’ve significantly enhanced digital experiences and contributed to in-depth technical discussions in the eLearning, Media, and Security sectors, showcasing a commitment to innovation and excellence in the digital landscape.